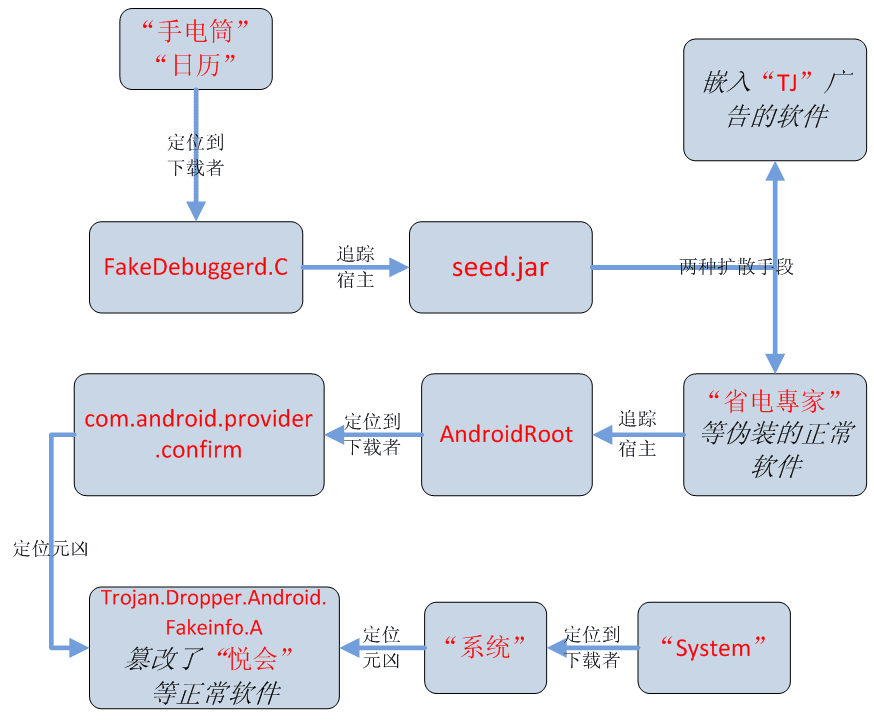
New ‘Fakedebuggerd’ vulnerability in all versions of Android OS upto lollipop, lets hackers root accessFakedebuggerd targets Android 4.x devicesModus Operandi
As per the 360 researchers, the Fakedebuggerd vulnerability enables a potential attacker to access an area that can be accessed only with system or root permissions. The vulnerability uses two known Android 4.x Privilege Escalation (PE) exploits, ‘FramaRoot’ and ‘TowelRoot’, to run code under root privileges and to install a root toolkit on the device. This allows the potential hacker to hide the code both from the Android user as well as the security solutions running on the devices. As such the hacker may inject any malicious App without users notice.
Fakedebuggerd targets Android 4.x devices
The vulnerability is of high risk as it gives serious privilege escalation to the handlers of malware and this is the first time the researchers have found out any Privilege Escalation vulnerabilities in Android 4.x. As said above, uses two exploits, TowelRoot’ and ‘FramaRoot’ together which means it has a higher rate of infection as well as higher chances of hiding itself from the AV engines aboard the users device. The Towelroot exploit is based on the futex() syscall vulnerability (CVE-2014-3153). This Linux vulnerability was discovered five months ago by Comex and affects almost all Android devices prior to Android 5.0 lollipop. The other exploit, Framaroot, is basically a rooting tool and based on several exploits for most Samsung, LG, Huawei, Asus and ZTE devices and more. The exploits which form the Framaroot are named after heroes of the popular JRR Tolkein triolgoy “The Lord of the Rings,” like Gandalf, Boromir, Pippin, Legolas, Sam, Frodo, Aragorn and Gimli. Almost all Android smartphones which are made by the above companies are able to execute Framaroot quite easily which makes Fakedebggerd very powerful vector.
Modus Operandi
Once the Fakedebuggerd vulnerability is exploited and the root toolkit is deployed on the infected device, malicious code to collects sensitive data like unique identifiers, device versions and network connectivity data. Additionally it will install unnecessary Apps like Flashlight and Calender without the users permission. The Fakedbuggerd is quite aggressive in its intent and uses extreme measures to keep them installed. Even if these Apps are removed by user using root privileges, the Fakedbuggerd reinstalls them automatically using the PE exploit. And as said above due the malware’s perfect hiding technique, simply deleting the suspicious apps wont work in this case. The Fakedbuggerd malware is a serious threat because of its ability to access root privileges and run malware laden codes on infected devices. In today’s world of convergence when the critical and confidential enterprise data and mobile phones are interconnected, Fakebuggerd can cause havoc unseen before. As of now no security solution or antivirus can detect this malware, therefore precaution is the best remedy against getting infected through this vulnerability.
Stay away from third-party and unverified APKs and use the official Google Play Apps for download. Even if you have to download a APK, stick with trusted and well-reviewed app developers. Beware fake advertisements (malvertisements) and phishing links on all forms of communication – SMS, email and social networks.
Resource : 360 Blog.