Google researchers discover a critical flaw in Network Time Protocol (NTP) which is being exploited in the wildNetwork Time Protocol (NTP)Attacks seen in the real world
Network Time Protocol (NTP)
Network Time Protocol (NTP) is a networking protocol for clock synchronization between computer systems over packet-switched, variable-latency data networks. In operation since before 1985, NTP is one of the oldest Internet protocols in use. NTP was originally designed by David L. Mills of the University of Delaware, who still oversees its development. NTP is intended to synchronize all participating computers to within a few milliseconds of Coordinated Universal Time (UTC) is designed to mitigate the effects of variable network latency. The NTP is maintained and updated by NTP.org Every computer has an internal clock which needs to be updated from time to time. The logical clock of every individual machine needs to be synchronized with other machines to facilitate communication over a network like the internet. You might have noticed that if your computer time is wrong beyond a certain threshold value, your machine cannot connect to the internet or return an error especially on pages that require time synchronisation. This time is maintained by using the NTP protocol. So we do not need to specify the importance of this protocol. According to the experts, all the versions of NTP prior to 4.2.8 are affected by the flaw.
Attacks seen in the real world
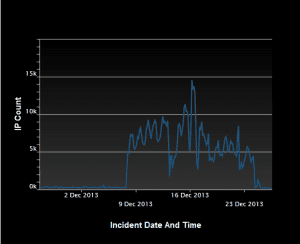
“Google Security Team researchers Neel Mehta and Stephen Roettger have coordinated multiple vulnerabilities with CERT/CC concerning the Network Time Protocol (NTP). As NTP is widely used within operational Industrial Control Systems deployments, NCCIC/ICS-CERT is providing this information for US Critical Infrastructure asset owners and operators for awareness and to identify mitigations for affected devices,” an advisory from ICS-CERT says. “These vulnerabilities could be exploited remotely. Exploits that target these vulnerabilities are publicly available.” Earlier 2014, security researchers at Symantec have spotted a series of Network Time Protocol (NTP) reflection DDoS attacks during the Christmas Holidays. In the following graph is reported the DDoS activity run by nearly 15000 IP addresses involved in the Network Time Protocol (NTP) reflection attack likely belonging to a botnet.
US-CERT has stated that exploitation of these NTP vulnerabilities may allow a remote attacker to execute malicious code. US-CERT encourages users and administrators to review Vulnerability Note VU#852879 and update to NTP 4.2.8 if necessary.